When using encryption to protect data for our cloud workloads, we have two primary scenarios to consider. Either the data is being transmitted to another recipient ("in transit"), or the data is stored ("at rest"). The protocols and algorithms used to encrypt the data will depend on which of these situations applies.
For example, consider a microservice that exposes a RESTful API for accessing data stored in a relational database. To protect the data while in transit, we use Transport Layer Security (TLS) for the API calls between clients and the microservice. But what about protecting the data when it is stored by the database?
With Amazon Relational Database Service (RDS), you can encrypt your data at rest by literally "checking a box". By enabling the encryption option for the database instance, RDS handles decryption of the data transparently, with minimal impact on performance.
However, you can only enable encryption when you create the database instance. Another limitation is that you cannot restore an unencrypted backup or snapshot to an encrypted database instance. What if you have an existing RDS instance that was created without the encryption option enabled? How can you update your database to have encryption at rest?
Luckily, there is an easy workaround to accomplish this. We can take advantage of the RDS feature that allows you to add encryption when making a copy of a snapshot.
To add encryption to an unencrypted RDS instance, perform the following 3 steps.
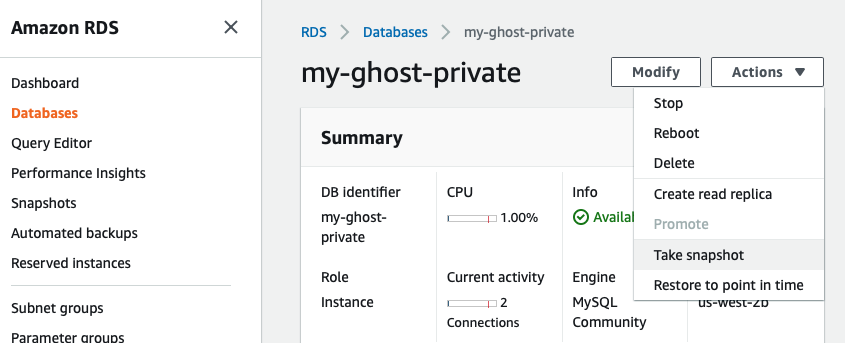
Step 1: Take a snapshot of the existing unencrypted database instance.
From the RDS Console, navigate to the database instance, and then choose "Actions->Take snapshot".
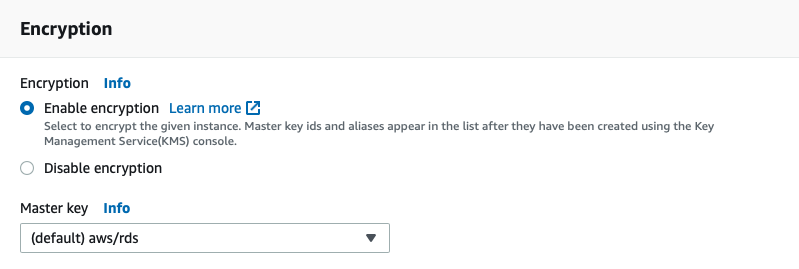
Step 2: Create a copy of the snapshot, enabling the encryption option.
Navigate to the list of snapshots, select the snapshot you just created, then choose "Actions->Copy snapshot". In the Encryption section, choose "Enable encryption" and then select the master key to be used. You can use either the default encryption key for Amazon RDS for your AWS account or you can opt for a specific KMS customer master key (CMK).
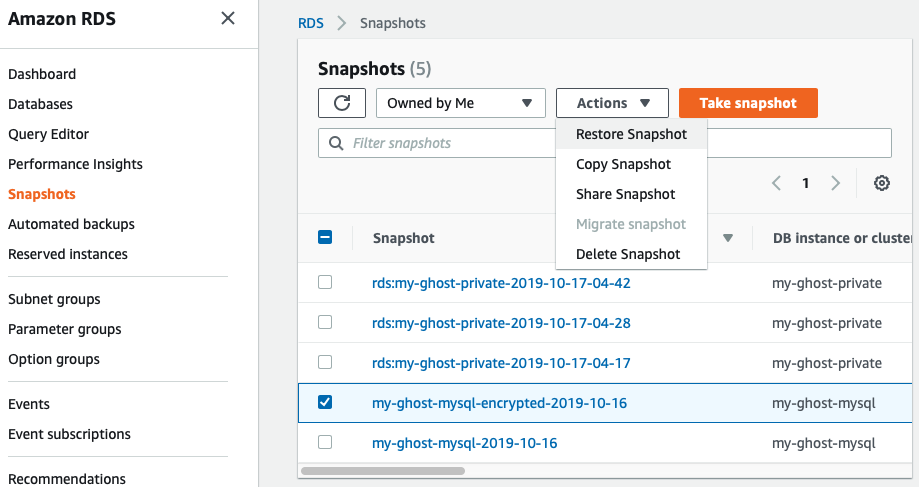
Step 3: Restore the encrypted snapshot to a new database instance.
From the list of snapshots, select the new encrypted snapshot, then choose "Actions->Restore Snapshot". Specify the details for the new instance, then click the "Restore DB Instance" button.
After the new database instance is available, you can then update your microservice to use the new RDS endpoint and then delete the original RDS instance.
Voilà! Your microservice now has full encryption, supporting both in transit and at rest encryption.


